Posted on Friday, 2nd April 2010 by Michael
Blue Coat URL Redirection Vulnerability
The Blue Coat web filter is one of the industry’s leading web filtering solutions. It provides the organization the ability to filter where their employee’s, vendors, customers or guests can go online.
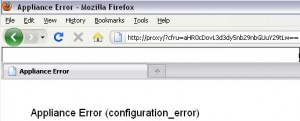
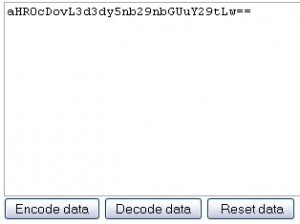
The Blue Coat Web filter has an issue where it will display a base64 encoded URL in the following format http://blue_coat_name/?cfru=aHR0cDovL3d3dy5nb29nbGUuY29tLw== when it has an error.
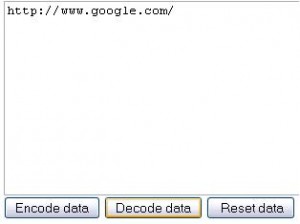
This URL is displayed in the end users browser usually with a message relating to the issue. The encoded URL is the URL that the end user was trying to get to before the error occurred. In the URL above I was trying to access www.google.com. To verify that we can use any base64 decoder, for this example I used an online version found at http://base64-encoder-online.waraxe.us/ .
All a malicious user would need to carry out an attack would be remote site that is hosting a malicious payload or an attack platform like Metasploit or Core Impact to host the malicious file. The attacker would than use a base64 encoder to encrypt the malicious URL and send the problematic link to the system administrator or any other end user. This attack could lead to a full system compromise depending on the payload and the rights of the user clicking the URL.
The limitation to this vulnerability is that DNS name and or IP of the Blue Coat web appliance will differ for the majority of companies. Though I bet there are at least a few companies out there that have named their Blue Coat web filter “proxy” or “webproxy”. By posting several of these generic names on the internet it may also be able to compromise other remote machines as well.
The question that I have to Blue Coat is why you would provide such functionality. Why don’t just display the URL in clear text.
Posted in Security Advisories | Comments (0)